Massive cyber attacks hit Asian hospitals, schools and universities
By Medha Basu and Nurfilzah Rohaidi
Software demands payment of $300 to return control of critical computing infrastructure.
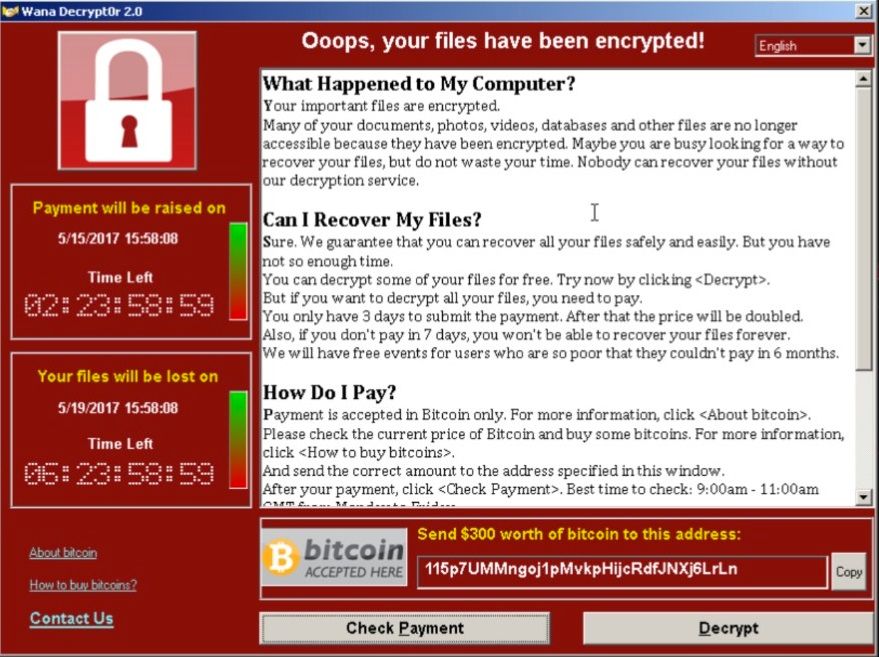
Image:Wikipedia
In Indonesia, two major hospitals, Dharmais Hospital and Harapan Kita Hospital in Jakarta, were affected. “Efforts to localise the infected server are underway to prevent (the ransomware) from spreading,” Semuel Pangerapan, a director general at Indonesia's Communication and Information Ministry told Reuters.
The ransomware - called WannaCry, WannaCrypt, WanaCrypt0r 2.0, or Wanna Decryptor - hit nearly all the computers in Dharmais Hospital. IT systems with patient records and billing were locked up, Abdul Kadir, president-director of Dharmais Hospital, told Reuters.
Some Japanese organisations were also affected, William Saito, cyber security adviser to the Japanese cabinet and trade ministry told Reuters.
University hospitals in Seoul have been affected, but officials are unclear whether it’s the same ransomware or other malware.
And schools and universities in China were hit, according to the country’s official news agency.
Meanwhile, there were no reports on breaches of critical infrastructure in the Philippines, officials said over the weekend.
The Cyber Security Agency of Singapore said that no government agencies or critical infrastructure were affected, according to the Straits Times, although some businesses were hit.
In total, the wave of global cyberattacks last Friday has hit over 200,000 targets in at least 150 countries, Rob Wainwright, the head of the European Union’s police agency has told the BBC, calling it “unprecedented in scale”. Russia and the UK are among the worst-hit. Germany’s rail network and Russia’s interior ministry were also affected.
The numbers may be under-reported in Asia, as most attacks took place between Friday evening and Saturday morning. In Japan, for instance, “I believe many companies have not yet noticed,” cyber security advisor Saito told the Japan Times. “Things could likely emerge on Monday” when people return to work, he added.
The ransomware, which blocks access to data until the user pays a ransom with Bitcoin, was combined with a worm application. This allowed the software to replicate itself and spread rapidly to other computers. The virus exploits a vulnerability in Microsoft’s Windows software, which was first identified by the US National Security Agency.
Organisations should ensure that their systems are updated and patched over the weekend, Wainwright added. Microsoft released a security update last month to address the weakness, and another one on Friday.
However, new variations of the ransomware have emerged as the hackers worked around temporary fixes, he said. A security researcher in the UK who helped slow down the attack has said that “another one is coming… quite likely on Monday”.
“The governments of the world should treat this attack as a wake-up call,” warned Microsoft President and Chief Legal Officer Brad Smith in a blog. “We should take from this recent attack a renewed determination for more urgent collective action,” he wrote.