Uncovering the unknowns: Rethinking endpoint defences in the age of AI-driven threats
By Dominic Cheah
Public agencies need to shift from reactive firefighting to real-time autonomous endpoint management to address the critical gaps and unknown devices that are currently exposing enterprise networks to risk.
-1760317421143.jpg)
Converged platforms unify endpoint management, risk and compliance monitoring, and incident response into a single autonomous platform. Image: Canva
In today’s era of rapid innovation, artificial intelligence (AI) is being weaponised by adversaries to accelerate the discovery and exploitation of vulnerabilities in enterprise defences.
These actors are leveraging AI to automate reconnaissance, identify misconfigurations, and launch sophisticated attacks at unprecedented speed.
This shift demands a fundamental rethinking of cybersecurity strategies. CIOs and CISOs must re-evaluate their defences across people, processes, and technology platforms to keep pace with evolving threats.
Generative AI is also being used to craft highly convincing phishing emails, deepfake content, and social engineering scripts. These tools mimic legitimate communication styles, making it harder for humans and traditional filters to detect malicious intent.
The speed and scale at which these AI tools operate will exceed human capabilities, necessitating a shift in how organizations defend themselves.
Visibility gaps in legacy endpoint tools
Legacy endpoint management tools operate at legacy speeds: slow, siloed, and reactive. They struggle to detect rogue devices, shadow IT, and misconfigured endpoints that are unknown to each tool.
These blind spots are the bane of cybersecurity, often invisible and unmanaged by IT. Adversaries often target these as valuable ingress points into enterprise networks.
For example, a misconfigured endpoint might quietly bypass patching policies, or an unmanaged device could be missing critical baseline security controls without detection.
These issues often put IT Ops and Cybersecurity teams into reactive firefighting mode all the time, unable to devote any time toward understanding and prioritising risks in the environment.
Unfortunately, even with a shiny new AI badge plastered on, these legacy tools are held back by their inherent hub-and-spoke architectures.
Their human operators are in turn frustrated and held back from responding any faster.
Real-time autonomous endpoint management: Beyond legacy endpoint tools
Real-time Autonomous Endpoint Management platforms go far beyond basic asset, patch and policy management. They provide granular insights into device posture, 3rd party application libraries, certificate configurations, and numerous other security controls.
For instance, they can detect if a device has disabled antivirus protection, is running vulnerable libraries, or has unauthorised applications installed. These platforms also continuously check for compliance, alerting teams to configuration drift that may expose the device to attack.
In research conducted across ASEAN, large enterprise organisations using such a platform have found up to 30 per cent of devices on their distributed networks were unknown and unmanaged.
These devices were unknown to the legacy tools and missing from their reports. These endpoints were missing critical patches and had outdated security controls, posing significant risks.
By surfacing these gaps in coverage, these organisations can remediate these issues swiftly and prevent potential breaches.
Silo teams & point tools: A barrier to agility
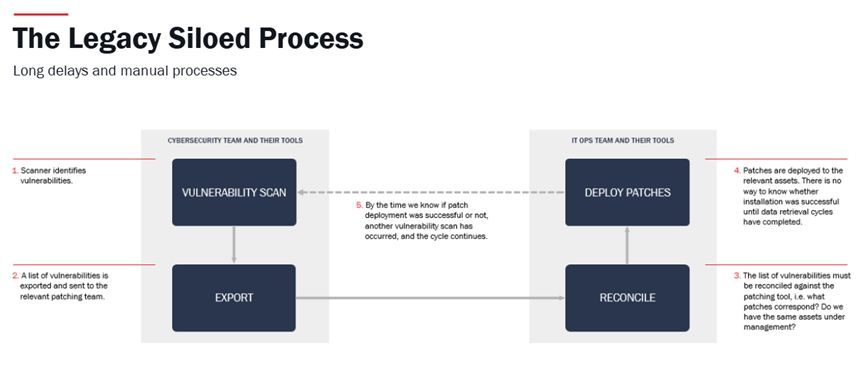
The traditional separation between IT Operations and Cybersecurity teams has created inefficiencies that adversaries exploit.
When cybersecurity teams identify a vulnerability, they often rely on IT Ops to deploy the fix. However, disparate tools and teams introduce delays and potential miscommunication.
This fragmented approach results in extended exposure windows, which give adversaries opportunities to exploit.
For example, a vulnerability on an endpoint flagged by the Cybersecurity team during a periodic scan may not be remediated promptly if the data from the patch deployment tool doesn’t reconcile with the data from the vulnerability assessment tool or if the remediation process is manual and error prone.
Such delays are unacceptable and unsustainable in an environment where threats evolve by the hour. Organisations must break down these silos and foster integrated workflows.
Converged endpoint platforms: A strategic imperative
Converged platforms unify endpoint management, risk and compliance monitoring, and incident response into a single autonomous platform.
CIOs and CISOs must adopt platforms that enable vast improvements in Mean Time to Identification (MTTI) and Mean Time to Remediation (MTTR) of any endpoint issue, regardless of ownership.
These platforms should provide real-time data that serves as a single source of truth for IT Ops, Compliance, and Cybersecurity teams, enabling seamless workflows and collaboration.
They should also support automated remediation workflows, allowing well-understood issues to be resolved with zero manual intervention if desired.
This level of automation is essential for maintaining resilience in the face of AI-driven threats.
Furthermore, converged platforms support role-based access controls, ensuring that each team can perform its duties without compromising security or compliance.
This operating model is critical because adversaries do not obey corporate segregation of duties.
Instead, they exploit opportunities presented by coverage gaps due to organizational structures.
A unified platform ensures visibility and governance across all endpoints, reducing the risk of exploitation.
As they implement new platforms, forward thinking organizations will constantly evaluate existing processes, seeking areas to streamline and reduce the MTTI and MTTR.
The combination of continuously improving people, process and technology platforms will be essential to stay ahead of the threat.
Endpoint visibility: Discovering the unknowns
A real-time Autonomous Endpoint Management platform is designed to uncover risks that traditional tools overlook.
The platform should be able to:
- Rapidly identify endpoints that are unknown and unmanaged by IT,
- Automatically bring such endpoints under management,
- Provide deep granular inspection of the endpoint state, including OS, applications, SBOMs, processes, IOCs, and more,
- Provide continuous inspection of endpoint security controls and configurations,
- Enable automated remediation to resolve non-compliance and vulnerabilities.
AI-augmented analysts: The future of cyber defence
Generative AI and AI agents are transforming how analysts operate. These tools can analyse vast datasets, identify patterns, and recommend actions.
They serve as force multipliers, enabling analysts to focus on strategic decision-making rather than manual data processing.
A critical consideration remains: the effectiveness of AI hinges on the quality of input data. Real-time, accurate endpoint telemetry is essential for training models and generating trustworthy insights.
This directly influences the performance of AI-driven automation playbooks, which are designed to extend the capabilities of limited human analyst teams.
To operationalise AI effectively, organisations must ensure their endpoint platforms deliver reliable, high-fidelity data.
Only then can automation respond correctly to endpoint conditions with speed and precision, enhancing security outcomes while easing the burden on limited human analyst resources.
From reactive firefighting to proactive governance
As adversaries continue to weaponise AI, the need for real-time visibility and proactive governance becomes paramount.
Re-architecting endpoint platforms with real-time visibility and proactive governance positions teams to significantly speed up response times across IT Ops, Compliance, and Cybersecurity.
By uncovering the unknown unknowns, CIOs and CISOs can transform their teams from reactive firefighting to proactive governance, ensuring visibility and compliance gaps are addressed before they become problems.
Join us at GovWare 2025
Join us at GovWare 2025 to experience firsthand how Tanium helps you navigate the cybersecurity challenges of this AI age and uncover the unknown.
Learn how an Autonomous Endpoint Management platform powered by AI can empower your teams to stay ahead of adversaries and strengthen your organisation’s cybersecurity resilience.
Dominic Cheah is the Director of Technical Solutions Engineering, ASEAN of Tanium. He has more than 20 years of experience in the cybersecurity field across different sectors spanning finance, aviation and global MNCs. He has designed and implemented scalable architectures to safeguard large enterprises, defence, and government organisations with up to hundreds of thousands of endpoints.